Risks of Using HTTP For Your Web Application
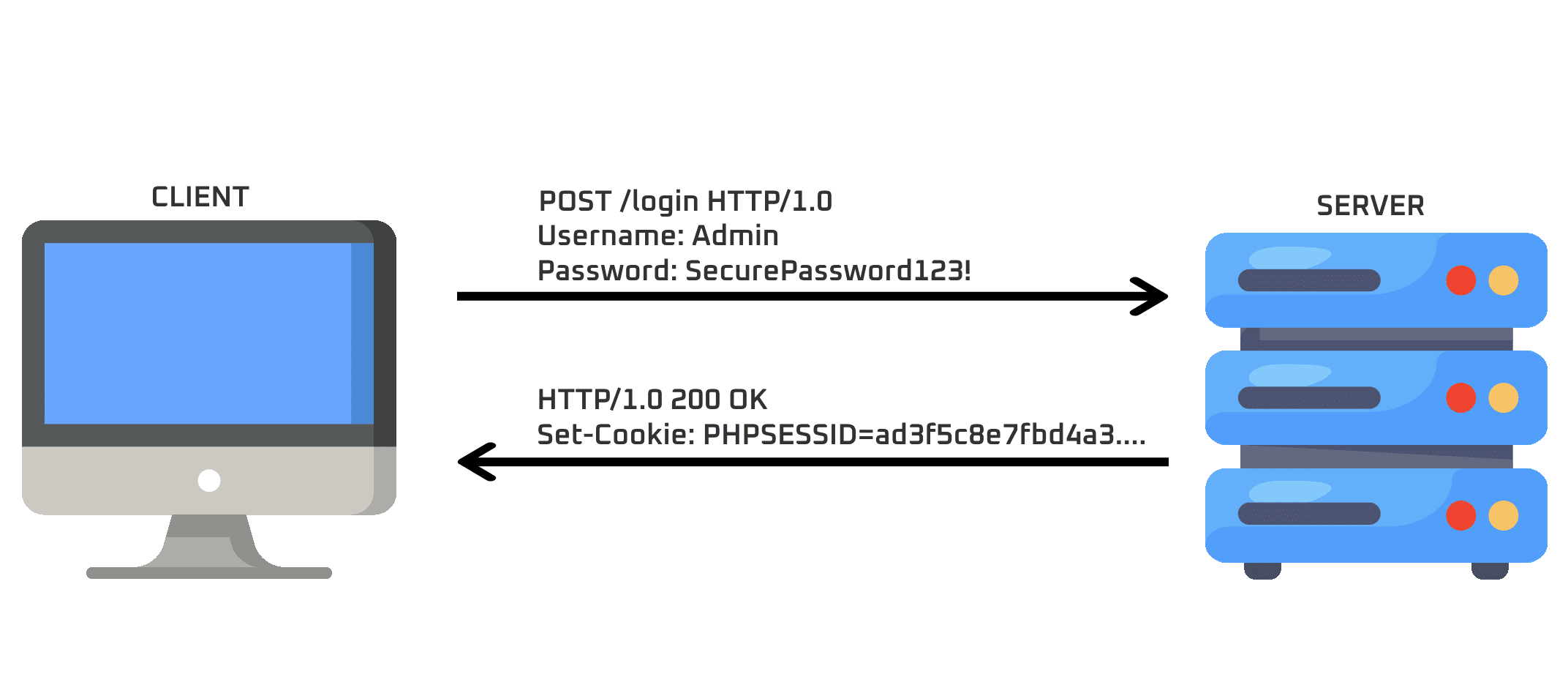
Risks of Using HTTP For Your Web Application For modern web applications, the average user will interact over a secure protocol for communication (i.e. HTTPS, or Hypertext Transfer Protocol Secure). However, it’s not uncommon to encounter a web application hosted in an internal corporate environment using the less secure HTTP (Hypertext Transfer Protocol) which communicates […]